Nigeria Security Awareness Information
The Threat to any state in Nigeria from the internal Terrorism Network is Substantial
Target Search Global Nigeria Security Advice….
The 5 C’s
- CONFIRM – the item is suspicious
- CLEAR – the area. Do not touch it.
- CORDON – off and secure the area.
- CONTROL – entry/exit to the cordon
- CHECK – for secondary devices.
THE H.O.T PROTOCOL
1. Confirm if the item is suspicious (Is it….Hidden?)
2. Obviously suspicious?
3. Typical of the surroundings?
- TARGET SEARCH GLOBAL NIGERIA SECURITY ADVICE…
- DO Not Use a RADIO or MOBILE Phone within 15 METRES of a SUSPICIOUS item
What is CSSML?
- CRITICAL – An Attack is expected immediately
- SEVERE – An attack is highly likely
- SUBSTANTIAL – An attack is a strong possibility
- MODERATE – An attack is possible, But Not likely
- LOW – An attack is unlikely
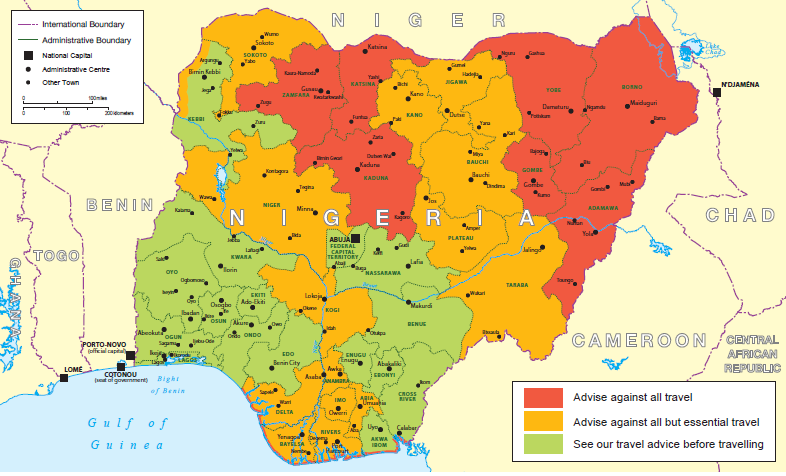
Map informing security situation to travel in Nigeria
THE 5 W’s
- WHERE – Is the suspicious item?
- WHAT – Is the suspicious item?
- WHEN – Was the item found?
- WHY – Is the item suspicious?
- WHO – Found the item?
CORDON DISTANCES:
- SMALL PACKAGE 100 Metres
- MEDIUM PACKAGE 200 Metres
- LARGE PACKAGE 400 Metres
Nigeria Security Global Risk Overview
1. Executive Snapshot
- Nigeria is experiencing a complex security environment characterized by insurgency, terrorism, organized crime, social unrest, criminal violence, and cyber threats.
- Key areas of concern include:
- Northeast: Regional insurgencies
- Northwest: Banditry
- Niger Delta: Oil-related violence
- Urban Areas: Rising crime rates
- The risk landscape is dynamic, influenced by evolving political, economic, and environmental factors.
2. Driving Risk Factors
- Governance Gaps: Inconsistent security provisions, corruption, and uneven public service delivery.
- Economic Pressures: High unemployment, inflation, and youth disenchantment can lead to unrest and opportunistic crime.
- Geographical Challenges: Porous borders and diverse terrains complicate security operations.
- Weapon Proliferation: Easy access to small arms increases the severity of incidents.
- Climate and Resource Stress: Desertification, flooding, and resource competition can lead to conflict and displacement.
- Cyber Risks: Increasing incidents of cybercrime and targeted misinformation campaigns affect businesses and public institutions.
3. Major Risk Categories
- Terrorism and Insurgency: Persistent threats in border areas; urban centers face spillover effects.
- Banditry and Violent Crime: Kidnappings, robberies, and rural attacks impacting safety and mobility.
- Communal and Ethnic Violence: Local conflicts driven by resource competition and political manipulation.
- Maritime Security: Piracy and theft along coasts disrupting trade.
- Infrastructure and Energy Security: Attacks on oil facilities and power grids leading to economic disruptions.
- Cybersecurity Threats: Financial fraud, ransomware, and assaults on critical infrastructure.
4. Sectors Most at Risk
- Transportation and Logistics: Vulnerable to ambushes and supply chain disruptions.
- Oil and Gas: Subject to facility attacks and personnel abductions.
- Public Sector: Risks linked to corruption and procurement issues.
- Financial Services: Vulnerabilities related to cybercrime and fraud.
- Healthcare and Education: Disruptions to services and safety concerns for staff.
- Telecommunications and Utilities: Challenges with service outages and data protection.
5. Impact Assessment
- Operational: Business interruptions and increased security expenditures.
- Financial: Asset losses and elevated insurance costs.
- Reputational: Increased scrutiny from stakeholders regarding risk management.
- Human: Direct risks to staff safety, displacement, and mental health issues.
6. Risk Mitigation and Resilience Strategies
- Governance Framework: Establish a formal risk management structure with regular assessments and oversight.
- Intelligence Operations: Invest in local intelligence and collaborative security efforts.
- Physical Security: Enhance access controls and secure facilities and transport.
- Crisis Response: Develop and practice emergency plans and response protocols.
- Cyber Resilience: Implement protections against cyber threats and enhance data security.
- Community Engagement: Foster relationships with local communities to address grievances.
- Continuity Planning: Establish measures for critical operations and supply chains.
- Training: Provide ongoing security awareness and specialized training for staff.
- Insurance: Ensure coverage for various risks, including cyber and business interruption.
7. Regional and International Collaboration
- Collaborate with government agencies, international security bodies, and industry associations to share intelligence and best practices.
- Coordinate with regional partners on cross-border security and disaster response initiatives.
8. Monitoring Indicators and Early Warning
- Threat Indicators: Track incident frequency, types, and locations.
- Patrol Metrics: Assess response times and incident containment success rates.
- Economic and Social Indicators: Monitor unemployment, migration trends, and public protests as warning signs.
9. Recommendations for Leadership Teams
- Elevate Awareness: Integrate security risk into strategic planning and budgeting processes.
- Foster Trust: Ensure transparency and engagement with stakeholders.
- Prioritize Safety: Provide robust health and security support for staff.
- Scenario Planning: Develop and test various “what-if” scenarios, including extreme disruptions.
- Transparent Communication: Deliver timely updates to partners and stakeholders.
10. Outlook
- Nigeria’s security landscape will continue to evolve in response to regional dynamics, economic conditions, and governance practices.
- Proactive, community-focused, and intelligence-led strategies will be essential in mitigating risks and maintaining operational continuity.
Would you like this tailored for a specific audience, or would you prefer it formatted as a slide deck with accompanying visuals and speaker notes? Please specify the intended length and tone, and I can adjust it accordingly.
