About Us
Driving Growth with Our Expertise and Passion
We provide professional services in all aspects of the security industry, but our core services cover the provision of event and leisure security, door supervision, close protection bodyguards, hostile environment protection, and corporate and retail security. Our solutions also include security consulting and training, security equipment sales, risk management, critical infrastructure security, and surveillance technology.

Strategic Risk Consulting
Risk Management
Executive Close Protection Operation

Reliable security services.
Trusted by Partners, Founders & Business Owners

Nigeria Police

Civil Defence

Halogen Group

TVC News

Channels TV

NTA

AIT

HI-IMPACT TV

NEWS CENTRAL

MTN

GTB BANK

FIRST BANK

KEYSTONE BANK

Western Coast Maritime Academy

STRONG AMON SECURITY

CAPTAIN IOJ SECURITY

CYBORG PROTOCOL

SHIELDFIELD PROTOCOL CONSULTING

RAMBO EXECUTIVE

KILOKITERON

Nigeria Police

Civil Defence

Halogen Group

TVC News

Channels TV

NTA

AIT

HI-IMPACT TV

NEWS CENTRAL

MTN

GTB BANK

FIRST BANK

KEYSTONE BANK

Western Coast Maritime Academy

STRONG AMON SECURITY

CAPTAIN IOJ SECURITY

CYBORG PROTOCOL

SHIELDFIELD PROTOCOL CONSULTING

RAMBO EXECUTIVE

KILOKITERON

Nigeria Police

Civil Defence

Halogen Group

TVC News

Channels TV

NTA

AIT

HI-IMPACT TV

NEWS CENTRAL

MTN

GTB BANK

FIRST BANK

KEYSTONE BANK

Western Coast Maritime Academy

STRONG AMON SECURITY

CAPTAIN IOJ SECURITY

CYBORG PROTOCOL

SHIELDFIELD PROTOCOL CONSULTING

RAMBO EXECUTIVE

KILOKITERON
Our Services
Advanced Threat Detection
Why Choose TSG Nigeria
Driving Growth with Our Expertise and Passion

Self Defence

Weapons Competency


Training

CSR
How Do We Operate?
We Provide Customized Security Solutions to Help Protect Your People
TSG specializes in Close Protection, delivering premium service to clients across corporate and high-risk environments. With over 20 years of experience, we safeguard individuals in both peaceful and hostile settings, and we provide comprehensive risk and threat assessments for organizations worldwide, including government bodies.
Executive Security Management
Target Search Global specializes in managing VIP risk while ensuring clients can carry on with their duties safely. Our experience spans a wide range of scenarios, including public engagements, private events, corporate executive protection, and personal or family escorting and chauffeuring.
Target Search Global Nigeria is a specialized training company with a proven track record in delivering security and medical training services. We are committed, capable, and competent to provide programs ranging from commencement-level courses to high-level professional security and crisis response training.
Bagging Certification in Governance, Risk and Compliance. Having undergone training from SIA and CompTIA Plus, TSG has positioned itself to handle cybersecurity, security analysis, IoT security, and a broad range of related services


























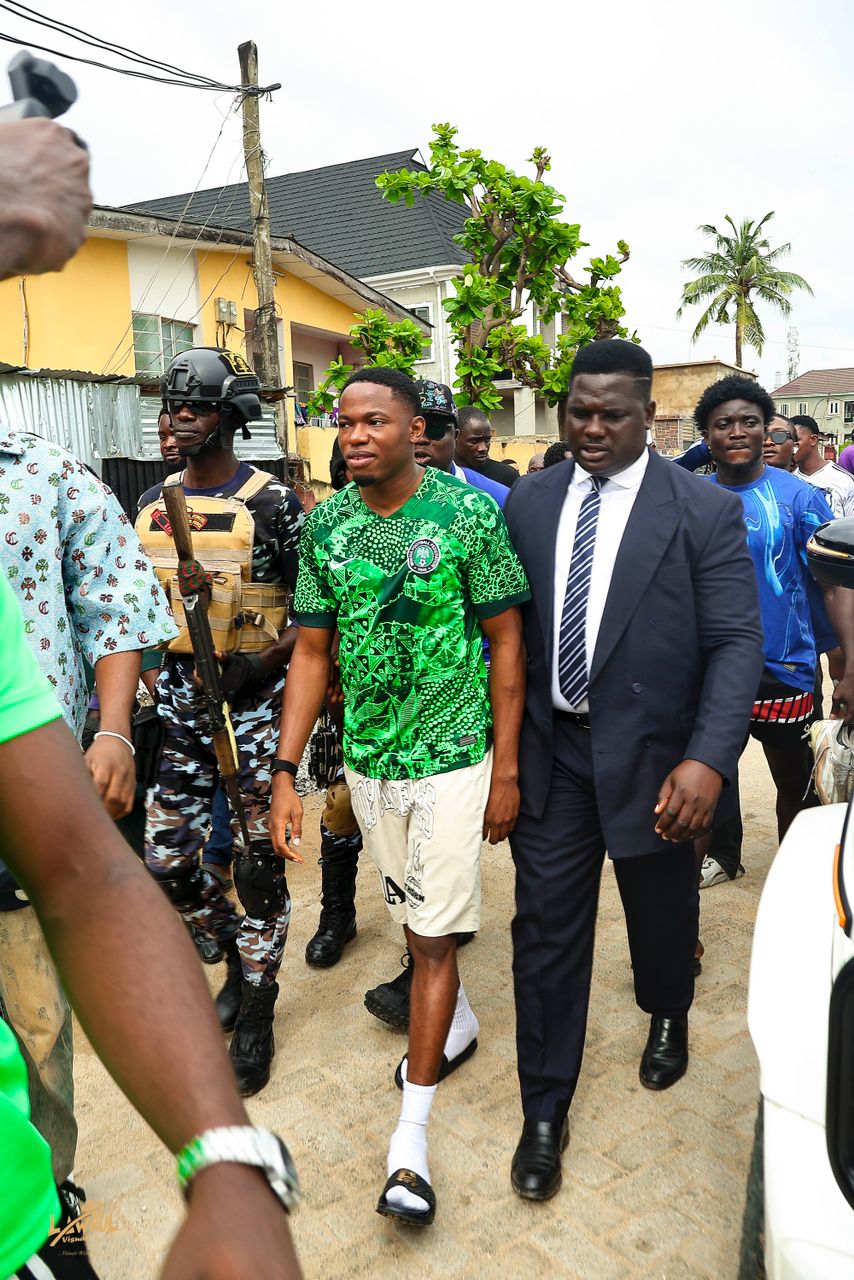


The Press
CEO Exclusive Media Session
How Do We Operate?
Advanced Cyber Network Security Solutions
Cybersecurity protection is the set of practices, technologies, and processes used to defend computers, networks, programs, and data from unauthorized access, damage, theft, or disruption. Its goal is to ensure the confidentiality, integrity, and availability of information and systems. Here’s a concise overview:
Key concepts
- Confidentiality: Keeping information private and accessible only to authorized people.
- Integrity: Ensuring data is accurate and has not been tampered with.
- Availability: Ensuring systems and data are accessible to authorized users when needed.
Main components
- Identity and access management (IAM): Methods to verify who users are and control what they can access.
- Network security: Firewalls, intrusion detection systems (IDS), virtual private networks (VPNs), and segmentation to protect traffic.
- Endpoint protection: Antivirus/anti-malware, EDR (endpoint detection and response), and secure configurations on devices.
- Application security: Secure software development, code reviews, vulnerability management, and runtime protections.
- Data protection: Encryption at rest and in transit, data loss prevention (DLP), and backups.
- Cloud security: Guardrails and controls tailored for cloud environments (identity, configuration, monitoring).
- Security monitoring and detection: Continuous monitoring, log management, and threat hunting to identify and respond to incidents.
- Incident response and recovery: Plans and teams for detecting, containing, eradicating, and recovering from security events.
- Governance and compliance: Policies, risk management, and regulatory adherence (e.g., GDPR, HIPAA, PCI DSS).
- Phishing and social engineering
- Malware and ransomware
- Hacking and zero-day exploits
- Insider threats
- Denial of service (DDoS) attacks
- Data breaches and exfiltration
Best practices
- Keep software and systems patched and up to date.
- Use strong, unique passwords and multifactor authentication (MFA).
- Regularly back up data and test restores.
- Segment networks and apply least-privilege access.
- Monitor and log activity; respond quickly to anomalies.
- Educate users and run phishing simulations.
- Develop and rehearse incident response plans.
Why it matters
- Protects sensitive information (customers, employees, intellectual property).
- Maintains trust and compliance with laws and regulations.
- Reduces financial and reputational risk from cyber incidents.
- Enables safer adoption of new technologies and digitization initiatives.
- Goal: Ensure compliance and reduce cyber risk from simple, daily actions to comprehensive, scalable controls.
- Levels:
- Simple daily practices: strong passwords/MFA, auto-updates, phishing awareness, regular backups, least privilege, secure Wi‑Fi.
- Foundational controls: asset inventory, IAM/RBAC, endpoint protection, network security, data protection, secure SDLC, basic security monitoring.
- Compliance-focused governance: risk management, policies, regulatory mapping, data governance, third-party risk, audit readiness, training.
- Advanced, scalable controls: zero trust architecture, PAM, XDR/CSPM, DevSecOps, incident playbooks, BC/DR, automation for evidence and monitoring.
- Roadmap (12 months): Baseline governance, identity/endpoints/data, network/protection, secure development/vendors, compliance alignment, testing/improvement.
- Metrics: compliance coverage, patch times, MFA adoption, incidents/MTTD/MTTR, backup recovery, phishing training.
- Next steps: tailor to industry, location, regulations; provide policies, templates, and a customized 12-month plan.

Used by 1200+ Customers
Unmatched Service, Unbreakable Digital Protection
- Digital Creator
Blessing Estella Moses
- C.E.O
Shekinah Glory TV
- Founder & Director
Paschal Jiwuobi


Our Blog
Explore Our Blog, Offers And Latest News
Discover how TSG transforms security and risk management with practical insights. Read our latest blog post, then book a meeting to discuss tailored strategies for your organization.








